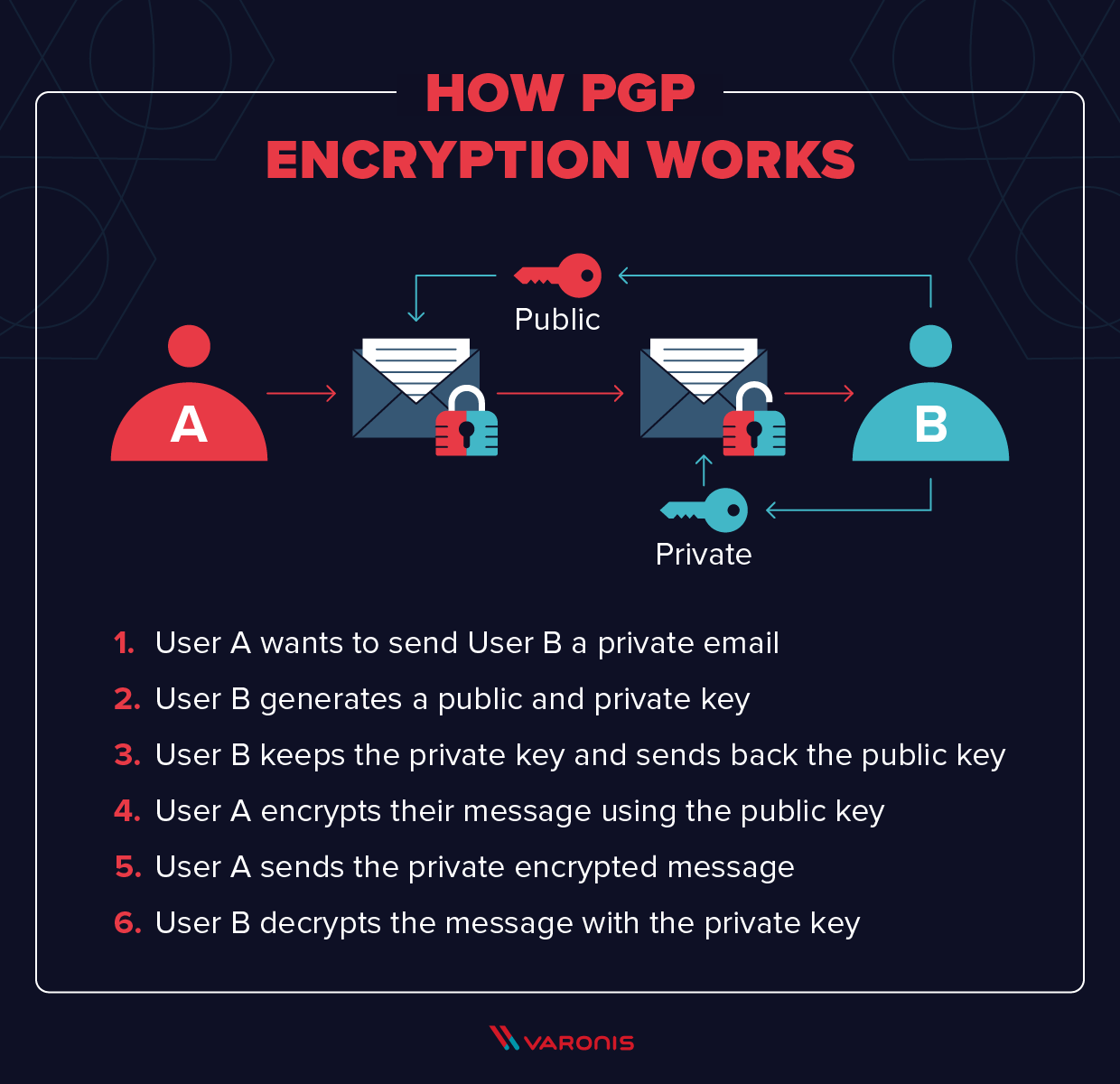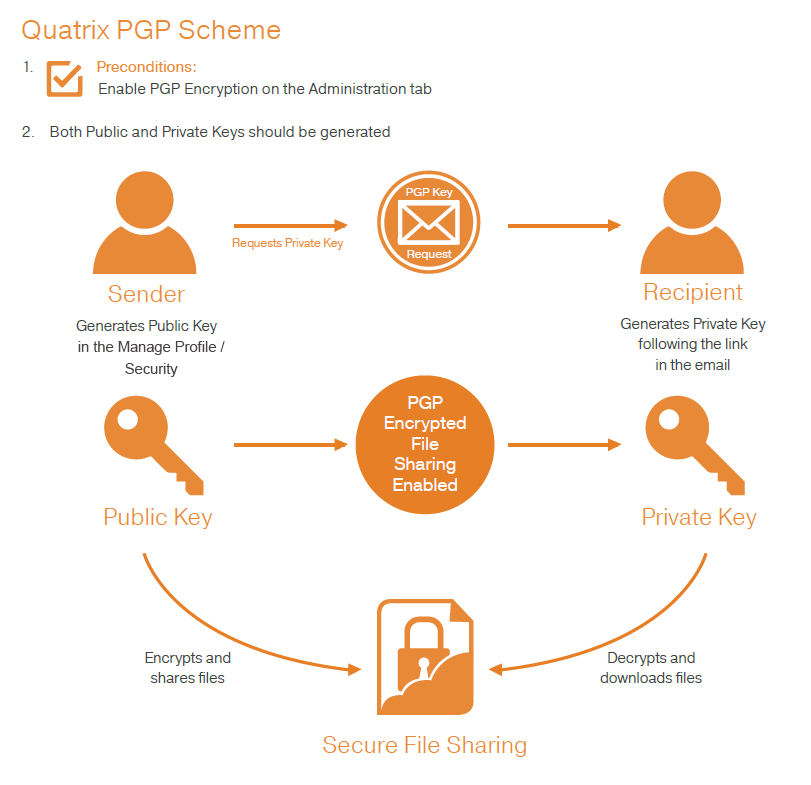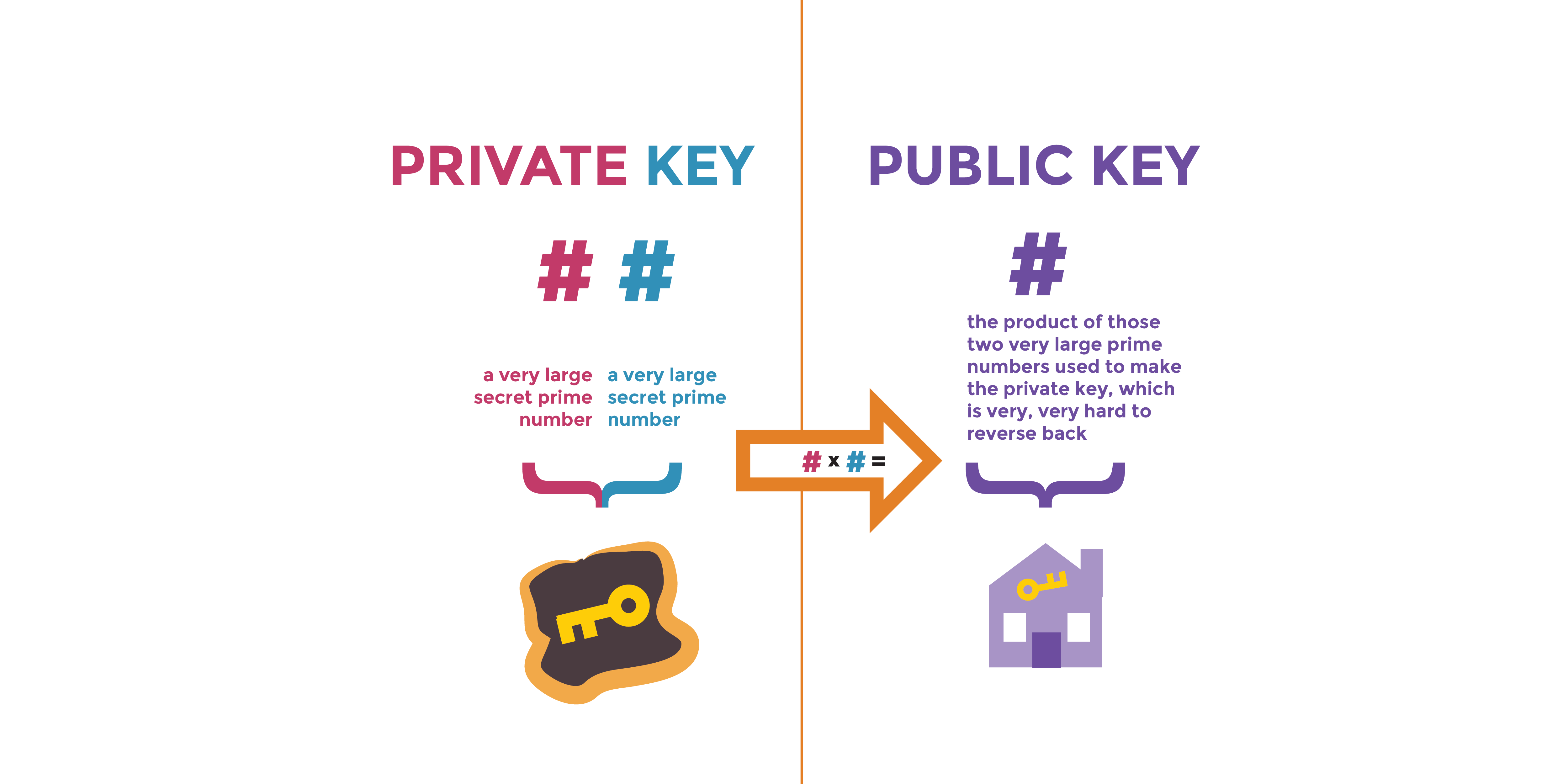
A Deep Dive on End-to-End Encryption: How Do Public Key Encryption Systems Work? | Surveillance Self-Defense
Using public-key crypto remains difficult – Networking notes – Recent articles, news and posts to help readers of the Computer Networking Principles, Protocols and Practice ebook to expand their networking knowledge